Setup OpenVPN in AWS for RDS access
When we use AWS, often we will use RDS, for security reason, is better to not to expose to public.
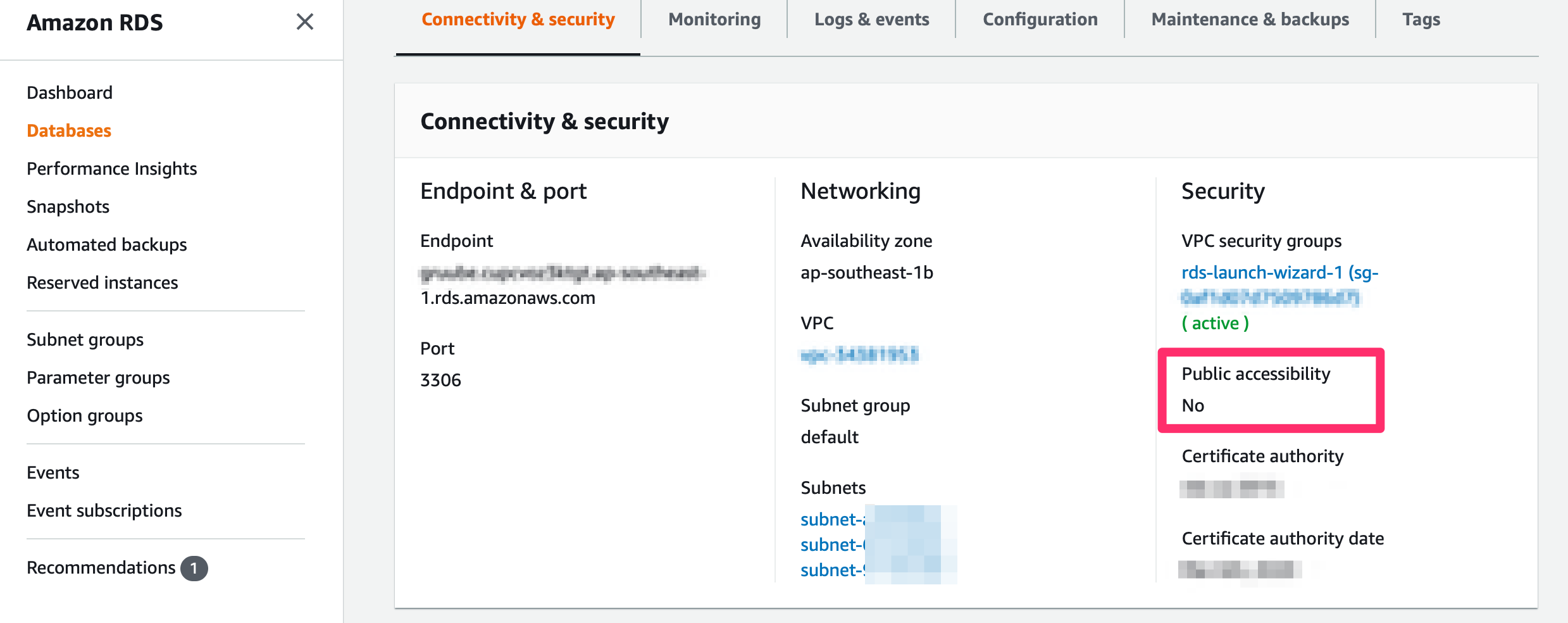
What if we want to access via MySQL client? Here’s why we need VPN.
1. Create an EC2 instance
After you created an EC2 instance (I chose Ubuntu 18.04), then create an elastic IP and associate with this instance.
Because we don’t want risk the IP to change when the instance restarted.
2. Follow this post.
1 | ubuntu@ip-172-xxx-xxx-xxx:~$ sudo bash openvpn-install.sh |
The first time, enter the private IP (should be auto populated), then 2nd time is the elastic IP.
Now, you still won’t be able to connect to VPN yet.
3. Create a security group
Because the new instance doesn’t open some ports by default, now let create.
In the inbound tab:
| Type | Protocol | Port Range | Source | Description |
|---|---|---|---|---|
| Custom UDP Rule | UDP | 1194 | 0.0.0.0/0 | |
| SSH | TCP | 22 | 0.0.0.0/0 | |
| Custom TCP Rule | TCP | 943 | 0.0.0.0/0 | |
| HTTPS | TCP | 443 | 0.0.0.0/0 |
Then go back to instance menu, select the OpenVPN instance, and associate the VPN security group.
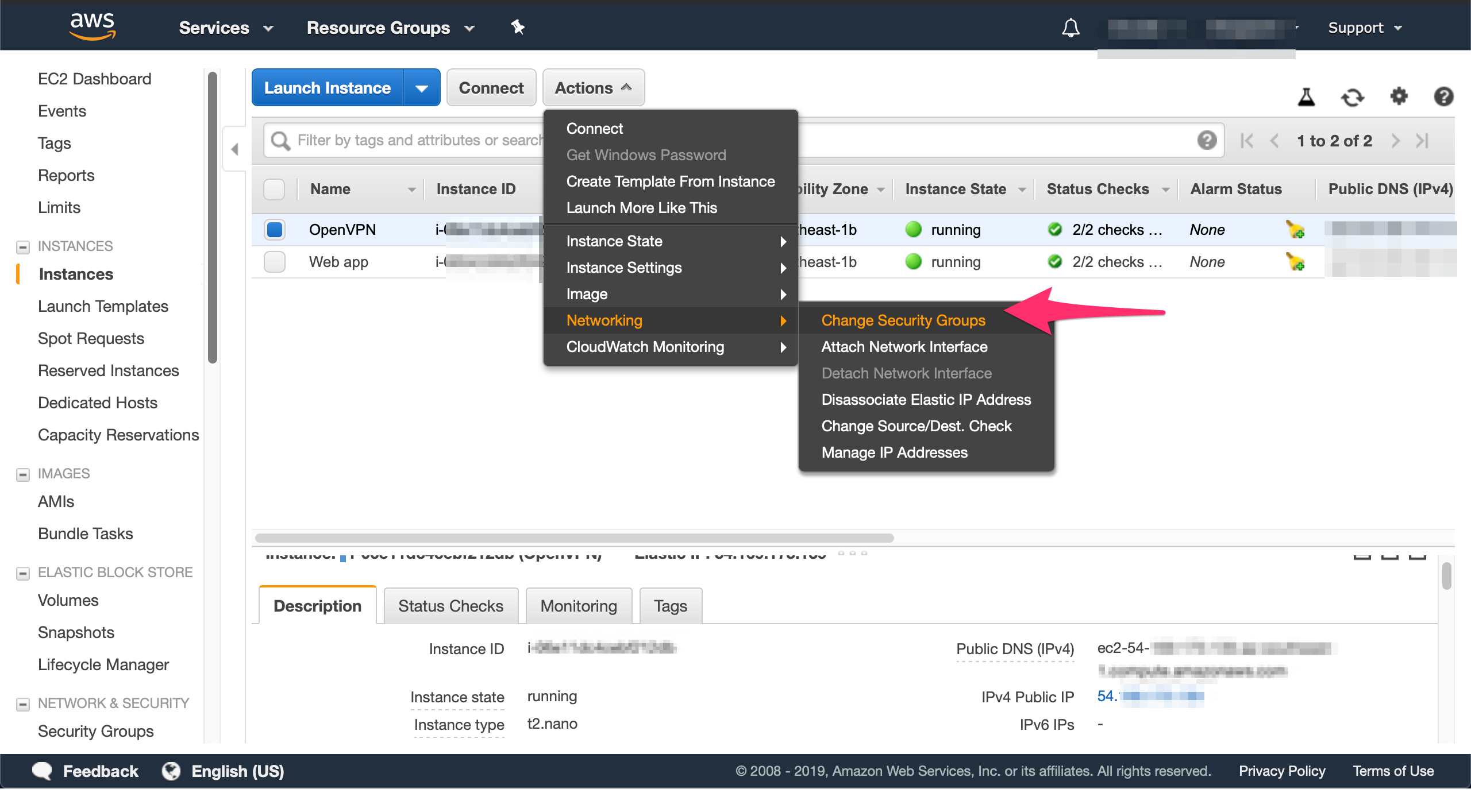
4. Update RDS security group
In the inbound tab
| Type | Protocol | Port Range | Source | Description |
|---|---|---|---|---|
| MYSQL/Aurora | TCP | 3306 | 172.xxx.xxx.0/24 | Web App |
| MYSQL/Aurora | TCP | 3306 | 172.xxx.xxx.xxx/32 | OpenVPN |
After this, you should be able to connect your local to VPN, and connect MySQL client to RDS.